Who are you?
Unwanted email is as near a certainty in life as death and taxes. “Selling” spam is a nuisance; phishing emails or messages bearing hostile attachments have the potential to really ruin your day. A lot of the time there are dead giveaways that the message isn’t what it appears to be – the grammar is usually poor, or perhaps the message is claiming to be from a company based in a foreign country that you’re unlikely to be doing business with.
We’ve all chuckled at poorly written messages, but what if the message looks like this?
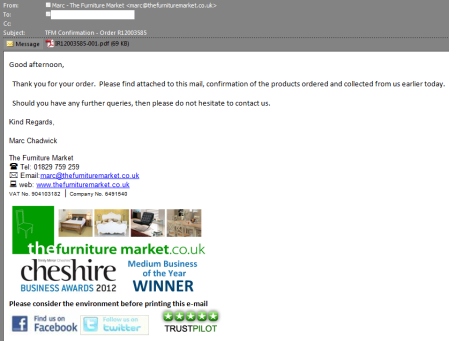 These are a little more convincing, because they’re copies of actual emails from these two companies – the companies, people and phone numbers all exist and are genuine. The messages are also targeted a little better – they claim to be from a UK company, and are sent to a recipient in the UK, meaning they’re more likely to be read and perhaps acted upon.
These are a little more convincing, because they’re copies of actual emails from these two companies – the companies, people and phone numbers all exist and are genuine. The messages are also targeted a little better – they claim to be from a UK company, and are sent to a recipient in the UK, meaning they’re more likely to be read and perhaps acted upon.
The attachments are of course not what they claim to be – the CDS message carries this; the Furniture Market message has this. Neither of these are things you want anywhere near your computer.
Messages like these cause two Problems:
Problem Number One is if a message like this was sent to, for example, your accounts department, would they consider it suspicious or would they open the (hostile) attachment without a second thought? After all, it seems legit – the usual red flags are mostly absent making the message more believable than most. However, if you go to the trouble of opening the attachment you’re running a definite risk of having your computer become part of a botnet, and at that point your real problems are only just beginning.
Problem Number One can be defended against in the usual ways:
- Educate your users – keep them vigilant. A legitimate looking invoice would have better provenance if you’d actually placed an order with the company it claims to come from. Do you do business with the sender organisation, regardless of how authentic the message looks? Context is important!
- Keep all your software patched and up to date
- Run current anti-virus (although as usual there’s no guarantee of success here, judging by the VirusTotal links above)
- Disable JavaScript in Adobe Reader
- Don’t log into your computer with admin rights
- etc!
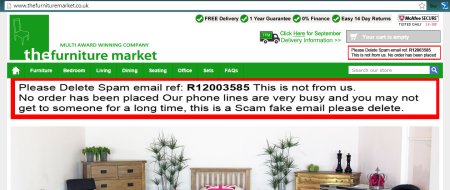
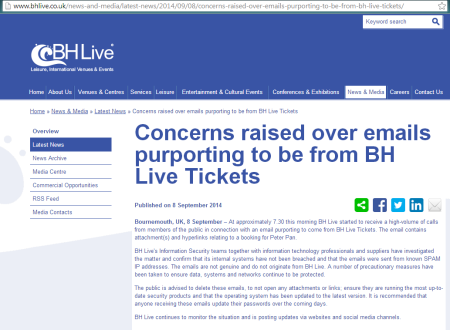
Problem Number Two affects the sender of the message. Not the actual criminal who sent the message, but the organisation the message claims to be from. Here are some very recent scrapbook snippings from the websites of affected companies:
…and the list goes on. The unfortunate companies above have done absolutely nothing wrong – they’ve not been hacked, they’ve not lost their customer lists, nothing – yet they’ve been forced to put prominent messages like these on their websites, and their customer service staff are suddenly inundated with calls and emails. Under the circumstances, it’s just about the best thing they can do – it shows they care by reassuring their customers that nothing’s been compromised, and hopefully it’ll decrease the load on their service staff. But it’s still not an ideal thing to have to put on the company website.
Is there an effective defence against this kind of impersonation? Email, by its very nature, is insecure (it’s the Simple Mail Transfer Protocol, after all) – it’s trivial to make an email appear to be from anyone you like. Copying an organisation’s email template is just the icing on the cake.
You could employ one or more of the following techniques:
- You could cryptographically sign each email you send, with a certificate and keypair you hold in your mail client. Certificates like this are often free.
- You could employ DomainKeys Identified Mail.
- You could use the Sender Policy Framework.
- You could sign up to EmailReg.org
All of these are mechanisms which are designed to detect email spoofing, as in the above examples. A shortcoming of this approach is that it is the reciever’s responsibility to do the checking. If you’ve set up SPF, for example, it’s all for naught if the receiver doesn’t do the SPF check. Think about your own email arrangements – does your receiving mailserver perform SPF or DKIM checks?
Problem Number Two can therefore affect just about anybody, regardless of how careful you are in setting up anti-spoofing measures. The best defence against Problem Number One probably lies with the acutal human being opening the email – take the advice of these guys and ask the question, “Who Are You?”

 Alec Waters is responsible for all things security at Dataline Software, and can be emailed at alec.waters@dataline.co.uk
Alec Waters is responsible for all things security at Dataline Software, and can be emailed at alec.waters@dataline.co.uk




19 September, 2014 at 14:06
[…] Via: wirewatcher […]